CyberInflight was present at Space ISAC in Colorado Springs on 8th April
Florent RIZZO and Matthias POPOFF were proud to present at the Members Only session a Review of global and Russian space cybersecurity ecosystems!

Over the past 2 years, the cyberspace ecosystem has undergone a profound transformation. The evolution of the threat landscape is prompting space stakeholders to structure themselves from organizational, technical, and regulatory perspectives.
This presentation aimed to provide an overview of the cyberspace ecosystem based on CyberInflight research.
Since the late 2010s, Russia’s cyberspace security ecosystem has been experiencing a new dynamic, accelerated by the outbreak of war in Ukraine. The aim here was to show how its evolution differs from Western ecosystems. The characteristics of this ecosystem have been presented, and its strengths and weaknesses have been determined and explained due to the post-February 2022 context.
Thank you to the people who joined, and don’t forget to stay tuned for the next event!
#SpaceISAC #SpaceSymposium #CyberInflight #CyberSpace
The team is growing
We’re thrilled to welcome Juliette Bignon, our new intern, in our CyberInflight’s team this week
She will help us for 5 months on our market intelligence studies. Juliette has an International Relations Master’s Degree from the Université Jean Moulin Lyon 3, specialized in International Risks Expertise
Welcome Juliette!

Cyber Resilience in Space Workshop – Belgian Science Policy Office
Belspo, as part of the Belgian Presidency of the Council of the EU, organized a panel on “Cyber Resilience in Space Workshop: Mapping Challenges, Forging Resilience”.
Two main things to remember from these 2 conferences :
– The imminent establishment of the EU Space ISAC
and
– The future publication EU Space Law which will support the resilience of our ecosystem

Cybersécurité Spatiale: Principes clés de l’intersection des domaines cyber et spatial
L’espace: la frontière finale de la cybersécurité
Nous sommes ravis de partager la tribune « Parole d’Expert » de Matthias POPOFF, analyste marché chez CyberInflight, publié par le CyberCercle.
Les enjeux majeurs en matière de cybersécurité appliquée au spatial y sont présentés, un sujet d’une importance capitale à une époque où la technologie et l’espace sont de plus en plus interconnectés.
Au programme :
– La jonction du cyber et du spatial au carrefour des compétences
– Le spatial à l’épreuve de la guerre en Ukraine
– L’état de l’art de la cybersécurité spatiale
– La place du cyberspatial dans la conduite des opérations
L’article est consultable sur: https://cybercercle.com/paroledexpert-matthias-popoff-cyberinflight-08092023/
#Cybersécurité #Espace #Technologie #Satellite #ParoleDExpert #Cybercercle

Space ISAC – Colorado Springs
DEFCON / Aerospace Village / Hack-a-Sat
Release of SPARTA version 1.4
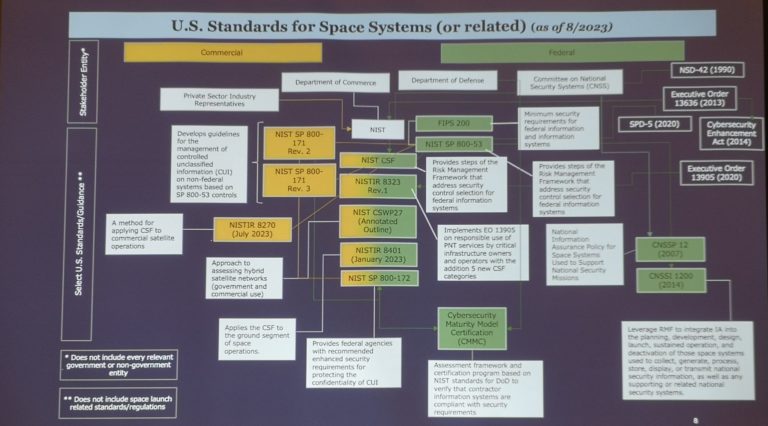
The evolution of SPARTA is a perfect illustration of how the cyber domain is increasingly taking into account the specificities of the space domain. This adaptation is carried out through multiple publications by NIST, MITRE and others. SPARTA is at the forefront of this trend and continues to include new elements to facilitate its use.
1- TTP Notional Risk Scores
Two objectives:
To establish the likelihood of an attack due to the uniqueness of every mission and system implementation.
To illustrate adversary capability which contributes to the likelihood that an actor can execute certain SPARTA TTPs.
In order to produce an analysis on the TTPs potential impact, this results in a NOTIONAL risk determination with three notional risk values sorted by system/mission criticality (high, medium, low).
2- ISO 27001 Mapping
SPARTA is adapting to other regional contexts and rules. This mapping was performed using NIST’s published mapping between NIST 800–53 rev5 and ISO 270001.
3- D3FEND Technique and Artifact Mappings
SPARTA aims to provide a translation/mapping of D3FEND (Denial, and Disruption Framework Empowering Network Defense) techniques from MITRE and artifacts to the relevant SPARTA countermeasures. This should enable users of SPARTA to bridge the gap between countermeasures/courses of actions (COAs).
4- Additional References
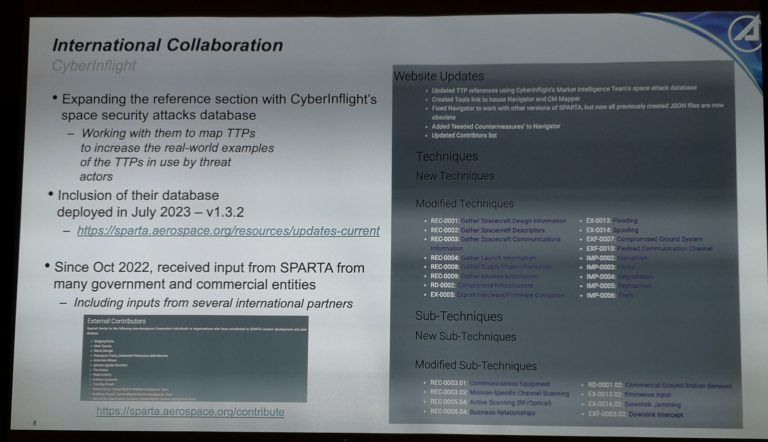
In SPARTA version 1.3.2, over 20 TTP references were updated using CyberInflight’s Market Intelligence Team’s space attack database. In version 1.4, the integration of our data has been fully completed. Approximately 50 attacks were added to the appropriate techniques/sub-techniques under the reference section for each TTP.
Roughly 60% of the attacks that we provided fall within the Reconnaissance and Resource Development tactics, which is a precursor to almost all attacks. This reinforces how important the Protect Sensitive Information countermeasure is because threat actors are actively extracting sensitive design information. In some cases, threat actors’ objectives are simply Exfiltration or Theft, and these attacks could be achieving their objective simply by stealing the information.
For more information, don’t hesitate to check the DEFCON31 presentation and SPARTA
Source: https://medium.com/the-aerospace-corporation/sparta-v1-4-whats-new-1ecdbf4873d7
#satellite #cybersecurity #cybersécurité #space